Nearly 300K Passengers’ PII in the UK and Ireland Were Exposed In Taxi Dispatch System Provider Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password-protected database that contained names, phone numbers, and email addresses of nearly 300,000 taxi passengers in the UK and Ireland. The records belonged to Dublin-based iCabbi, a dispatch and fleet management technology provider.
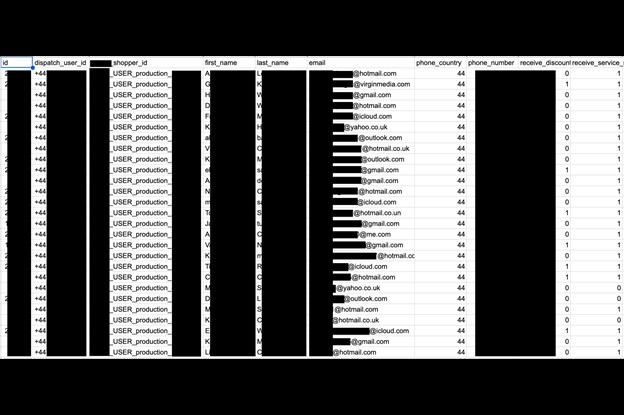
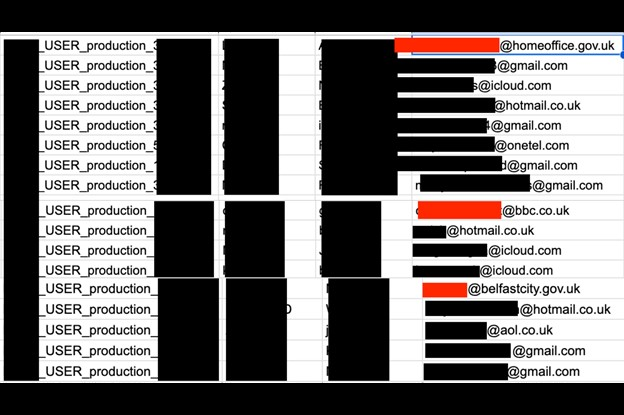
The non-password-protected database contained 22,745 records and.csv (comma-separated values) documents with the names, emails, phone numbers, and user IDs of nearly 300,000 customers based in the UK and Ireland. The exposed email addresses ranged from various email providers as well as private domains, including: 117,231 Gmail, 65,060 Hotmail, 17,588 Yahoo, 18,099 iCloud, 12,798 Outlook, 7,484 Live, and numerous other email accounts. I also saw email addresses from media outlets such as the BBC and government agencies, including the NIH, HM Treasury, Ministry of Justice, and numerous local and regional government departments. The files also included around 2,000 ac.uk university email addresses. These accounts appeared to be unique and I did not see any duplicates.
Upon further research, it was identified that the records belonged to a company called iCabbi, which provides a taxi dispatch platform technology for taxi services and passengers. I immediately sent a responsible disclosure notice of my findings, and public access was restricted the following day. It is unclear how long the data was exposed or if anyone else may have accessed the non-password-protected database. Only an internal forensic audit would identify any additional access or suspicious activity.
The database appeared to be a content management storage repository for documents used by the application, such as terms and conditions files and spreadsheets with customer data. The folder that contained the exposed records also contained a large number of other documents that were secured and denied public access. As an ethical security researcher, I never bypass authorization credentials and only view documents that are publicly accessible to anyone with an internet connection. The potential risk of cyber criminals knowing the file paths of where documents are stored could allow a targeted brute force attack against the wider network or identifying individual misconfigured documents. I am not saying iCabbi’s network was at imminent risk, but I am providing a hypothetical risk of exposing the file path where customer documents are collected and stored.
In response to my disclosure notice an iCabbi representative replied with transparency and professionalism: “Thanks again for bringing this to my attention - we have deleted the records. Human error to blame here unfortunately... part of a migration of customers but we should not be using public folders. We are going to engage with customers to make them aware of this breach”.
Founded in 2009, iCabbi is owned by Nottinghamshire-based Exel Technology Group. iCabbi claims to be the first to introduce the Software-as-a-Service (SAS) model to the taxi industry by offering services that include a dispatch system, applications for passengers and drivers, IVR phone systems, payment solutions, API, and a partner marketplace. According to iCabbi’s website, the company has registered over one billion bookings across 15 countries (though all of the exposed records I saw pertain only to individuals based in Ireland and the UK). iCabbi’s technology is intended to modernize and manage taxi services and to be competitive with ride-hailing companies. In 2023, the taxi operation industry in the UK was valued at an estimated £8.6 billion.
Taxi Industry Data Risks
One extreme example of how taxi dispatch information could be used in cyber crimes happened in New York a few years ago, when two Americans and two Russians compromised the taxi dispatch system at John F. Kennedy International Airport. Once they had access to the dispatch data, they sold places in the front of the dispatch line to cab drivers. Drivers would often have to wait hours before their turn in line and not earn any money during this time. The group indicated they intercepted over 1,000 taxi trips per day for nearly two years. Although it is not clear exactly how the dispatch system was compromised, the indictment indicates the group discussed bribing someone to use a USB drive to inject malware, using WiFi to intercept packet data, or even stealing a laptop that was connected to the dispatch system. In this real-world example, the criminals targeted and profited from taxi drivers and not riders, but it shows how creative cyber criminals can be when it comes to financial gain. Although this case is not related to the iCabbi exposure, it identifies that there is a history of the taxi industry being at risk.
Potential Risks of Exposed User Data
Any data breach where potentially sensitive user information or PII (including names, emails, and phone numbers) is compromised poses a possible risk for the affected customers. Hypothetically, criminals could exploit this data for various malicious purposes. When criminals know the specific services that customers use as well as their contact details, they have sufficient information to engage in targeted phishing campaigns. In this case, for example, I was able to search for specific domain names such as “.gov.uk” and identify individuals who work at local, regional, and national government agencies. These individuals could potentially be higher-value targets compared to the average passenger, depending on the motives behind the hypothetical attack. In 2023, ransomware attacks made up over 23% of all cyber incidents affecting personal data in the UK. The lack of precautionary measures has made it so that, in the parliamentary committee’s words, the British government is at high risk of a “catastrophic ransomware attack”.
Hypothetically, the most common tactic would be criminals sending mass emails to users under the false pretenses that the email is an official communication from a legitimate taxi service using iCabbi’s technology. Cybercriminals could potentially target these individuals to get them to reveal additional personal information, financial or credit card details, passwords, and more.
After a data exposure, it is important that users are aware of what was exposed and how that data may be used by malicious actors. It is also important that customers stay vigilant and verify the legitimacy of any requests for additional personal information or payment data. I recommend that anyone who receives suspicious messages always contact the company through official channels. Never click on any links or download attachments from unexpected emails, as these may contain malware or additional phishing attempts. By being cautious and verifying the authenticity of any unexpected communications or information requests, individuals can add additional layers of security to protect themselves from potential threats that may originate from a data breach. I am not saying that any iCabbi users or their customers were or are at any risk. I am only providing a plausible scenario of how exposed data could be used if malicious actors were to obtain this information.
Although contact information alone is not as sensitive as passwords or financial details, there are numerous potential cybersecurity risks that go beyond phishing attacks and social engineering. More technical tactics could include techniques like credential stuffing where criminals could potentially identify previous data breaches that may contain known customer email addresses and reused passwords to gain unauthorized access to the user’s accounts. I highly recommend that users enable Two-Factor Authentication (2FA) to enhance security against unauthorized account access, even in cases where criminals possess partial account information or even passwords. Being vigilant, monitoring your accounts, and knowing when to be suspicious or verify information requests can assist mitigating the risk of malicious activities or becoming the victim of a cyber attack.
I imply no wrongdoing by iCabbi, their partners, clients, or customers. I am also not saying the data was at risk or accessed by any other individuals. iCabbi acted fast and professionally to secure the data upon receiving my responsible disclosure notice. As an ethical security researcher, I manually review a limited number of files to ensure accurate and responsible reporting, but I never download or extract any data. My goal is always data protection and education. I believe the general public should be aware of how scams work so they can minimize the risk of falling for cyber criminals’ tactics.